The new threat BlackRock malware detected. Android Users Beware!
Discovered by ThreatFabric, this malware has stolen personal data from 337 apps including Netflix, YONO Lite by SBI, Gmail, and more.
Many apps belonging to different fields – Finance, social, information, lifestyle, etc. are targets of this new malware.

As we all love net-surfing and malware is not on our acceptable-list, obviously, alertness is needed.
So, read this article to find out how Blackrock malware acts and steal.
The Internet has made our lives much better and enjoyable, but there are a lot of issues we should be aware of, while net-surfing.
One of these problems is malware. They threaten the safety of our device and information. Thus, one needs to be aware of it.
Read also – https://theqna.org/corona-virus-can-be-transmitted-via-air-claim-239-scientists-in-an-open-letter-to-who/
With rising cybercrimes, self-awareness is the best protection.
Currently, new malware has terrorized android, with its ability to steal data, passwords, and financial information through several apps.
About May 2020, ThreatFabric analysts had discovered new distress of banking malware, that is dubbed BlackRock.
It looked pretty familiar to them. And so they examined it.
After analysis, it became apparent that this new threat originated from the code of the Xerxes banking malware.
The old Xerxes, a strain of the LokiBot Android banking Trojan, seemingly provided the code for the new headache, Blackrock.
But there are several features unseen before.
BlackRock, unlike other Android trojans, targets more apps and it has targeted around 337 apps.

It steals login information and also urges its prey to enter their credit card details if their apps authorize monetary transactions.
In a report, conveyed to ZDNet, researchers asserted that the vast majority of BlackRock overlays target financial and social apps.
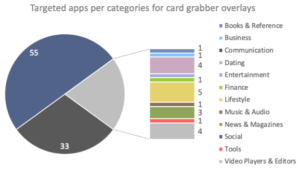
ThreatFabric, the one who detected this new threat, says that
” BlackRock collects data by a method called ‘overlays’.
This method includes observing a user’s interaction with a legitimate app.
When the apps open, it shows a fake window to the user to collect the login and card details before permitting the user to use the real app.”
In other words –
As it appears in the guise of the app, people fail to realize its fakeness, they enter their login and card credentials which reach the hacker.
The moment credentials are provided, the users can access the app. And, the BlackRock malware escapes without any trace of data-stealing.
About its overlay method, ThreatFabric explained,
“Once the user grants the requested Accessibility Service privilege, it starts by granting itself additional permissions.
Those additional permissions are required for the bot to fully function without interacting any further with the victim.
When done, the bot is functional and ready to receive commands from the C2 server and perform the overlay attacks.”
Some apps that became a target of the BlackRock malware are –
- PayPal mobile cash,
- Gmail,
- Yahoo Mail,
- Microsoft Outlook,
- Amazon seller,
- Skrill,
- Uber, Netflix,
- Amazon shopping,
- Binance,
- YONO Lite SBI,
- IDBI Bank Go Mobile+,
- iMobile by ICICI
To perform overlay, BlackRock functions like most Android malware and uses familiar old techniques like others.
Once installed, an app, contaminated with the BlackRock malware, asks for access to the Accessibility feature of the phone.
The Accessibility feature, is a powerful feature of Android, as it can automate jobs and even operate on the user’s behalf.
BlackRock uses the Accessibility feature to access clearance and then uses the device policy controller, to gain admin access to the device.
It then utilizes this entry for its malicious overlays.
BlackRock can also conduct other ‘intrusive’ operations like –
- Dynamic Overlaying
- Key-logging(Key-log functionality)
- SMS fraud: sending, listing, and forwarding SMS without permission, spam messaging
- Collect Device data and avoid Anti-Virus
- Some Remote actions, like Screen-locking
- Even Self-protection: Hide its app icon, preventing the detection
- Collect Notifications and grant unauthorized approvals
Presently, BlackRock is circulating in the appearance of bogus update packages, requested by third party sites.
Luckily it hasn’t turned up on Google PlayStore till now.
However, be aware, Android malware gangs usually find ways to evade Google’s app review process.
Thus, so at one point or another, it’s likely that we see BlackRock deployed in the Google PlayStore.